Zero Trust Architecture for Microservices: Why It Matters and How to Implement It
Zero Trust Architecture is a critical security model for modern microservices. By verifying every request, enforcing least privilege, and encrypting internal traffic, Zero Trust helps prevent breaches and secures complex, distributed systems by design.
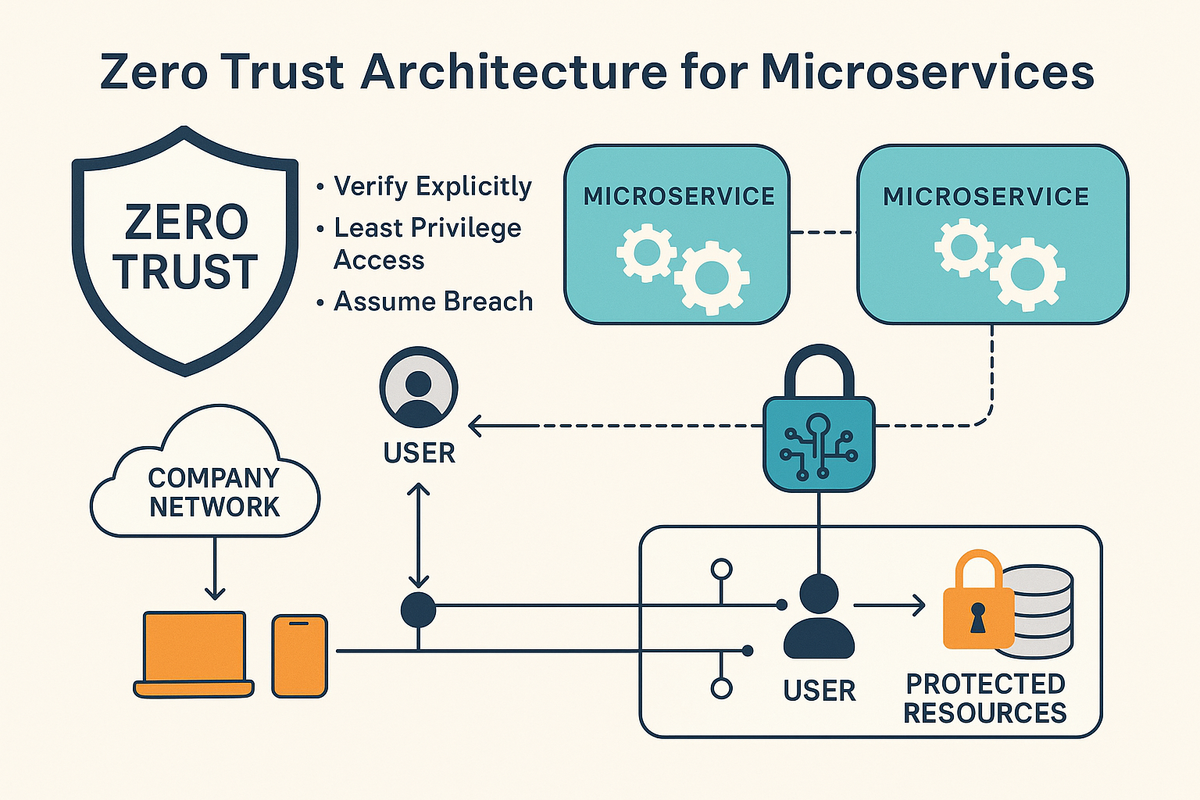
As organizations increasingly adopt microservices for building modern, scalable applications, traditional network security models fall short. Zero Trust Architecture (ZTA) has emerged as the go-to strategy for securing distributed systems like microservices.
In a Zero Trust model, the guiding principle is simple: “Never trust, always verify.” No user, device, or service is automatically trusted, regardless of whether it’s inside or outside the network.
This blog explores what Zero Trust means for microservices, why you should care, and how to implement it effectively in your architecture.
Why Zero Trust for Microservices?
Microservices often:
- Run on dynamic environments like Kubernetes
- Communicate through APIs over potentially insecure networks
- Integrate third-party services, making perimeter-based security ineffective
Zero Trust ensures continuous verification of identities and strong access controls for every service-to-service interaction, not just external requests.
Key Components of Zero Trust in Microservices
1️⃣ Identity Verification
Use strong service identity with mTLS (Mutual TLS) for all internal communication.
2️⃣ Least Privilege Access
Each service should have only the minimal permissions required to perform its function. Implement with RBAC (Role-Based Access Control) or ABAC (Attribute-Based Access Control).
3️⃣ Micro-Segmentation
Isolate workloads at the service or pod level in Kubernetes. Tools like Istio, Linkerd, or Consul help manage service mesh security.
4️⃣ Continuous Monitoring
Implement observability and alerting on all communications between services using tools like Prometheus, Grafana, and ELK Stack.
Tools to Implement Zero Trust in Microservices
| Component | Tools |
|---|---|
| Identity & mTLS | Istio, Linkerd, SPIFFE/SPIRE |
| Access Control | Open Policy Agent (OPA), Kyverno |
| Monitoring | Prometheus, Grafana, Jaeger |
| Secrets Management | Vault, AWS Secrets Manager |
Example Architecture: ZTA in Kubernetes
- Service mesh (e.g., Istio) for mTLS between pods
- OPA/Gatekeeper for enforcing access control policies
- Centralized logging & tracing with ELK or Grafana Loki
Conclusion
Zero Trust isn’t just a buzzword—it’s a security strategy that fits naturally with microservices. By assuming that threats can come from anywhere and verifying everything at every step, organizations can reduce risks while maintaining agility.
With microservices, Zero Trust is not optional—it’s essential.