Shift-Left Security in Microservices Development: Why, What & How
hift-Left Security brings security earlier into the development of microservices. By identifying vulnerabilities in design, code, and pipelines, teams reduce risks and fix issues early. It’s essential for secure, scalable, and fast microservices delivery.
In the rapidly evolving world of microservices, security is no longer something that should be addressed only at the end of the development process. Enter Shift-Left Security—an approach that embeds security early in the Software Development Life Cycle (SDLC). For microservices architecture, this is not just a good practice—it’s essential.
In this blog, we’ll dive deep into Shift-Left Security, why it matters for microservices, and how you can implement it effectively.
What is Shift-Left Security?
Shift-Left Security is a proactive approach where security practices are integrated early in the development cycle—starting from design, coding, and build phases—rather than being addressed later during testing or deployment.
Traditional security models operate like a "shift-right"—security checks happen after code is written. In contrast, "shift-left" ensures developers write secure code by design and catch vulnerabilities before they reach production.
Why Shift-Left Security is Crucial in Microservices
Microservices break large applications into smaller, independently deployable services. While this enables flexibility and scalability, it also increases the attack surface.
Here’s why Shift-Left Security is especially important for microservices:
1️⃣ Multiple Attack Surfaces: Each service could have its own API, database, or authentication layer.
2️⃣ Rapid Deployment: CI/CD pipelines push code frequently. Delayed security can’t keep up.
3️⃣ Third-Party Dependencies: Microservices often rely on open-source packages, which can have known vulnerabilities.
4️⃣ Increased Complexity: Managing security at the integration level is harder when hundreds of services interact.
How to Implement Shift-Left Security in Microservices
Here’s a practical, step-by-step guide to embedding security from the start in your microservices development:
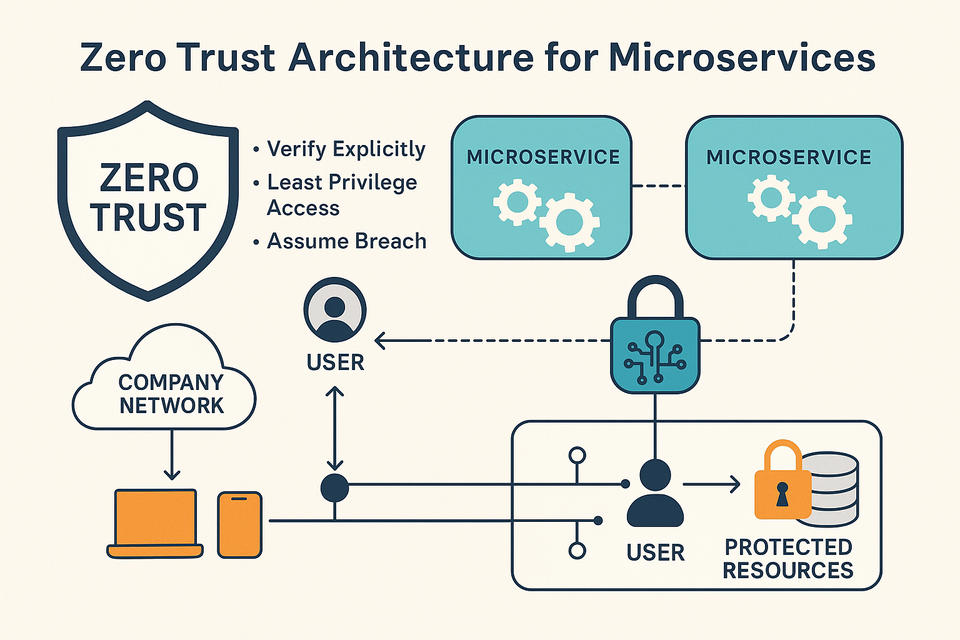
1️⃣ Secure Design Principles (Threat Modeling)
- Conduct threat modeling during the design phase.
- Use methodologies like STRIDE (Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, Elevation of privilege).
- Define secure communication between services (e.g., mTLS, OAuth2).
2️⃣ Secure Coding Practices
- Train developers in OWASP Top 10 vulnerabilities.
- Follow secure API design principles (input validation, proper authentication, rate limiting).
- Implement Secrets Management—never hardcode credentials in source code; use solutions like HashiCorp Vault, AWS Secrets Manager, or Kubernetes Secrets.
3️⃣ Automated Code Scanning
- Use Static Application Security Testing (SAST) tools to catch security flaws during code reviews.
- Popular SAST tools: SonarQube, Semgrep, Checkmarx, CodeQL (GitHub).
4️⃣ Dependency Scanning
- Microservices depend heavily on third-party libraries.
- Use Software Composition Analysis (SCA) tools like Snyk, Dependabot, or OWASP Dependency-Check to identify known vulnerabilities (CVEs).
5️⃣ Container and Infrastructure Security
- Container Image Scanning: Tools like Trivy or Aqua Security can scan Docker images for vulnerabilities.
- Enforce least privilege in container runtimes (e.g., rootless containers).
- Use Infrastructure as Code (IaC) security scanning with tools like tfsec for Terraform or Checkov for cloud resources.
6️⃣ CI/CD Pipeline Security
- Integrate security checks directly in your CI/CD workflows.
- Example tools:
- GitHub Actions + CodeQL
- Jenkins + Snyk
- GitLab CI + built-in security scans
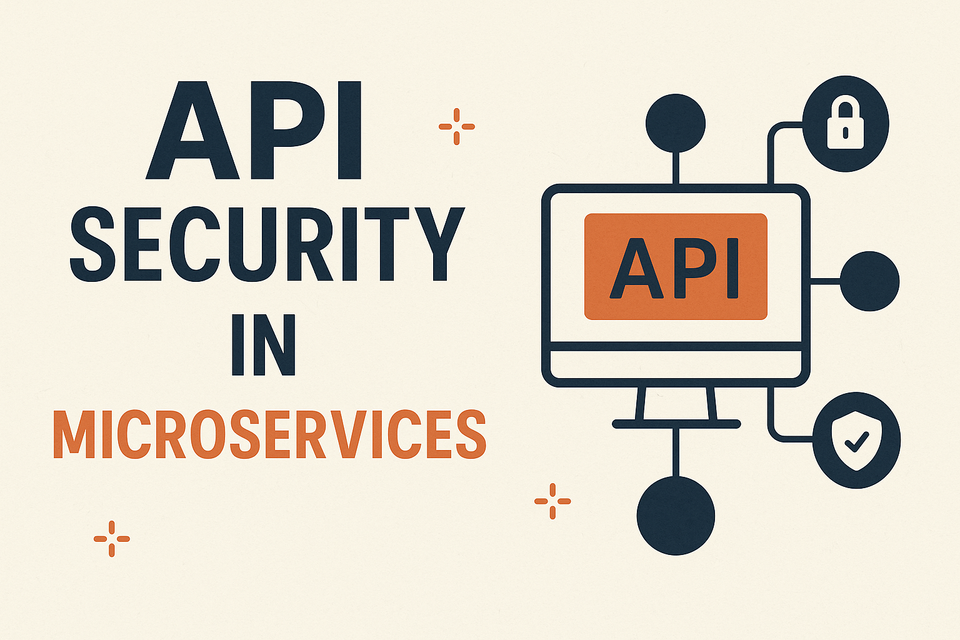
7️⃣ API Security Testing
- Perform Dynamic Application Security Testing (DAST) with tools like OWASP ZAP or Burp Suite against your running services.
- Validate rate limits, authorization, and input sanitization in APIs.
8️⃣ Runtime Security and Observability
- Implement Security Information and Event Management (SIEM) solutions to monitor threats.
- Use service mesh (e.g., Istio, Linkerd) for encrypted service-to-service communication.
- Set up alerting for unusual behavior (e.g., with Prometheus + Grafana).
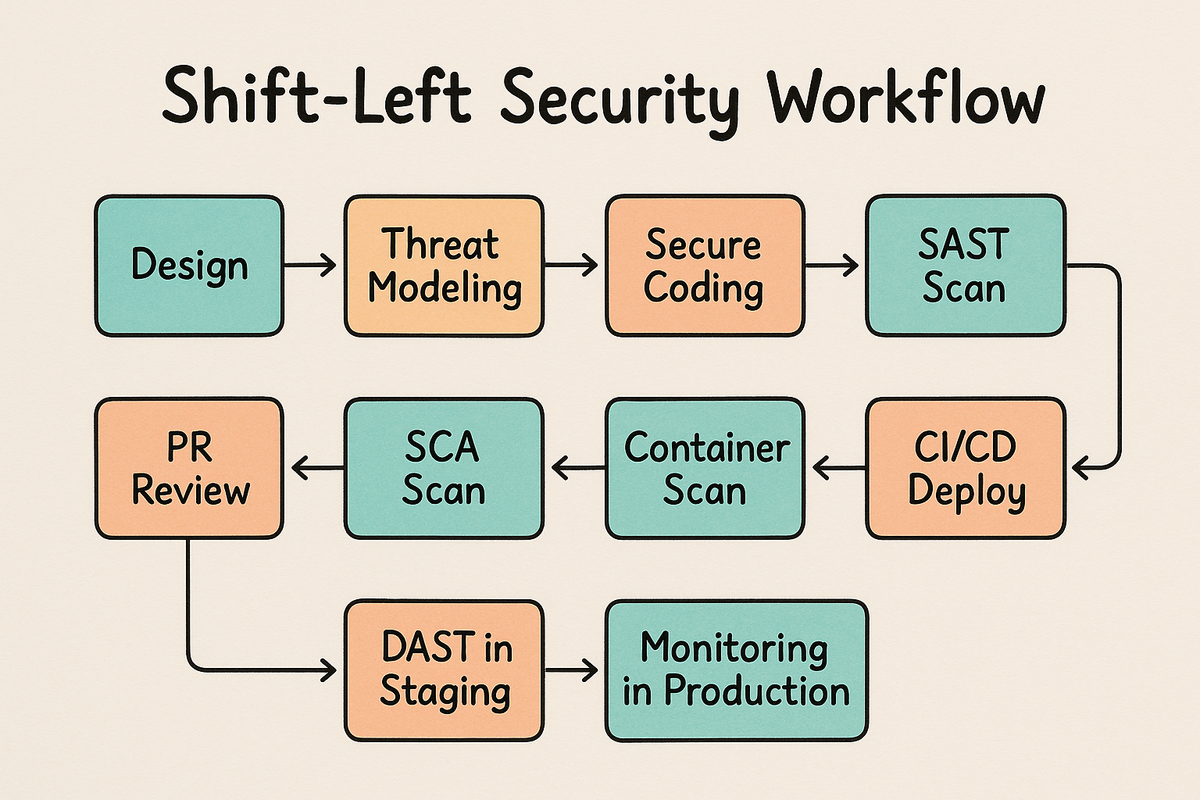
Real-World Example Workflow
Here’s what a Shift-Left Security flow looks like in a modern microservices project:

Tools to Start With
| Category | Tools |
|---|---|
| SAST (Code Scan) | SonarQube, Semgrep, CodeQL |
| SCA (Dependencies) | Snyk, OWASP Dependency-Check, Dependabot |
| DAST (API Security) | OWASP ZAP, Burp Suite |
| Container Scan | Trivy, Clair, Grype |
| Secrets Management | HashiCorp Vault, AWS Secrets Manager |
| IaC Scanning | tfsec, Checkov |
Benefits of Shift-Left Security in Microservices
- Reduced Cost of Fixing Vulnerabilities: Bugs caught early are cheaper to fix.
- Faster Time to Market: Avoids delays caused by late-stage security issues.
- Improved Developer Awareness: Security becomes a shared responsibility.
- Continuous Compliance: Helps meet regulatory and security standards earlier.
Conclusion
Microservices architecture demands a security-first mindset, and Shift-Left Security is the answer to that need. By integrating security from the very start, you build resilient, compliant, and trustworthy systems—without sacrificing speed.
Start small: integrate one security tool in your CI/CD this week. Gradually expand to a full-fledged DevSecOps practice.
Security is not a phase. It’s a mindset. Shift left today.