API Security in Microservices: Best Practices & Tools
APIs are the backbone of microservices, but without proper security, they become easy targets for attackers. From authentication to encryption, learn how to secure your APIs and protect your microservices architecture from evolving threats.
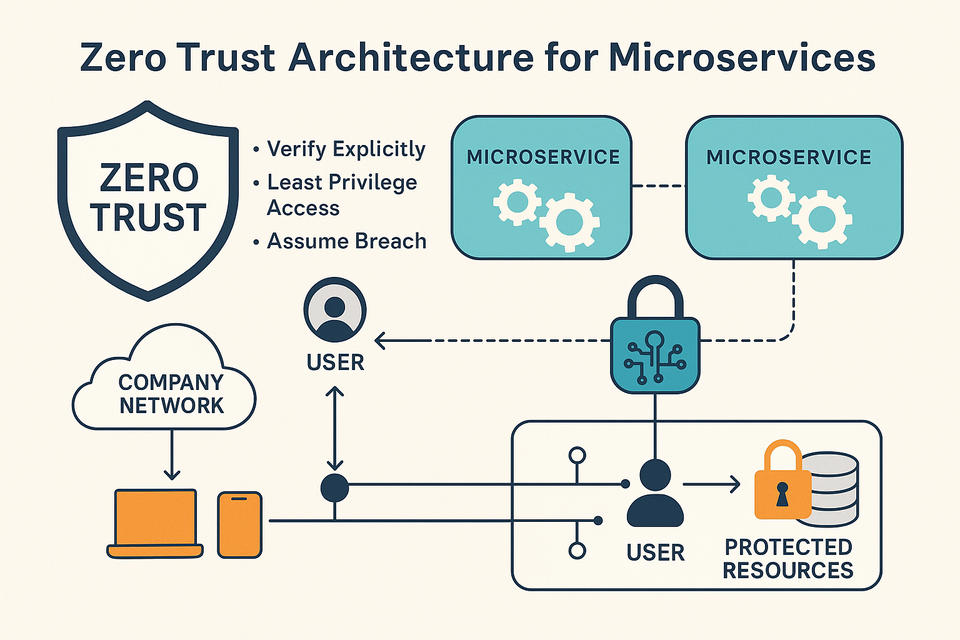
In a microservices architecture, APIs are the lifeline. Each microservice typically exposes an API to communicate with other services or external clients. This makes APIs a prime target for attackers. Securing APIs is not optional—it’s critical.
In this blog, we’ll explore why API security matters in microservices, common threats, and actionable strategies to secure your APIs effectively.
Why API Security Matters in Microservices
Microservices offer flexibility, scalability, and faster development cycles. However, they also increase the number of entry points into your system. If APIs aren’t properly secured, attackers can exploit these weaknesses to:
- Expose sensitive data
- Perform unauthorized operations
- Launch denial-of-service (DoS) attacks
- Lateral movement to attack other services
Because microservices rely on APIs to communicate, API security is microservice security.
Common API Security Threats
1️⃣ Broken Authentication
Improperly secured tokens or API keys.
2️⃣ Excessive Data Exposure
APIs returning more data than necessary.
3️⃣ Lack of Rate Limiting
Allowing unlimited requests can lead to DoS attacks.
4️⃣ Injection Attacks
Malicious input affecting database queries or commands.
5️⃣ Insecure API Endpoints
Publicly exposed APIs without authentication or encryption.
Best Practices for API Security in Microservices
1️⃣ Authentication & Authorization
- Use industry standards like OAuth 2.0 or OpenID Connect.
- Prefer JWT (JSON Web Tokens) for stateless authentication.
2️⃣ API Gateway Implementation
- Use an API Gateway like Kong, NGINX, or AWS API Gateway to centralize authentication, rate limiting, and routing.
- Enable mTLS (Mutual TLS) for service-to-service communication.
3️⃣ Input Validation & Output Encoding
- Never trust input. Use strong validation libraries.
- Sanitize data before sending responses.
4️⃣ Rate Limiting & Throttling
- Prevent abuse by setting API usage limits.
- Example: Allow only 100 requests per minute per user.
5️⃣ Encryption Everywhere
- Use HTTPS for all API communications.
- Encrypt sensitive data both in transit and at rest.
6️⃣ Secrets Management
- Store API keys and secrets securely using tools like HashiCorp Vault or AWS Secrets Manager.
- Never hardcode secrets in the source code.
7️⃣ Logging & Monitoring
- Enable detailed logging for all API calls.
- Use centralized logging (e.g., ELK stack, Grafana Loki) and alerting to detect abnormal activities.
Useful Tools for API Security
| Purpose | Tools |
|---|---|
| API Gateway | Kong, NGINX, AWS API Gateway |
| Security Testing | OWASP ZAP, Burp Suite |
| Rate Limiting | API Gateway features, Envoy |
| Secrets Management | Vault, AWS Secrets Manager |
| Monitoring | Prometheus, Grafana, Sentry |
Example: Securing an API in Kubernetes
1️⃣ Deploy your API behind NGINX Ingress Controller.
2️⃣ Enable TLS termination at the ingress.
3️⃣ Use OAuth2 Proxy for authentication.
4️⃣ Enforce rate limiting with NGINX annotations.
5️⃣ Scan APIs with OWASP ZAP regularly.
6️⃣ Monitor requests with Prometheus and Grafana dashboards.
Conclusion
APIs are the front door to your microservices. Without proper security, that door is wide open. By implementing best practices—secure authentication, encryption, rate limiting, input validation, and continuous monitoring—you can dramatically reduce risks.
Securing APIs is not a one-time task—it’s a continuous process aligned with DevSecOps practices.
Secure APIs, secure microservices, secure business.